What can we do before a security incident happens? What can we do after a security incident has happened? Our expert Mario de Felipe addresses this topic in the second post of the five in the series that we are dedicating to the options that AWS offers to guarantee the security of SAP workloads.
After a first article focused on Identity and Access Management, this new post is about Detective Controls and Incident Response, services that share the same objective. AWS refers to “Detective Controls” the actions we do to gain visibility to spot issues before they happen, improve our security posture and reduce the risk profile of our environment.
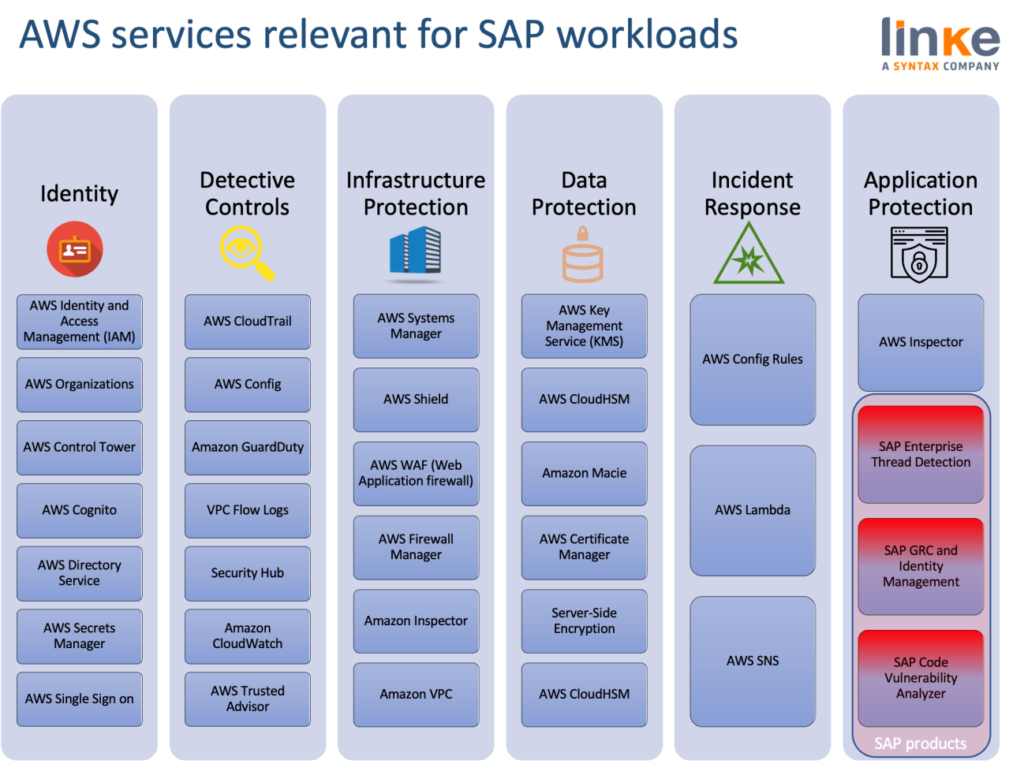
It’s much about monitoring. We can use logging features in AWS to determine the actions users have taken in our account and the resources that were used. The log files show the time and date of actions, the source IP for an action, which actions failed due to inadequate permissions, and more.
These are some of the keylogging features available in AWS:
- Amazon CloudWatch is the most important monitoring solution in AWS. It monitors our AWS Cloud resources and the SAP applications running AWS. We can set Amazon CloudWatch Monitoring for SAP NetWeaver ABAP-based environments and SAP HANA environments. Please see blog post SAP Monitoring: A serverless approach using Amazon CloudWatch by AWS Engineer Marcel Toerpe for more details.
- AWS CloudTrail logs every AWS API call and related events made by or on behalf of an AWS account. The AWS API call history produced by CloudTrail enables security analysis, resource change tracking, and compliance auditing. Also for every notification on access, we can use Amazon Simple Notification Service (Amazon SNS) to set up notifications on SSH login to our email address or mobile phone.
- AWS Config provides detailed historical information about the configuration of our AWS resources, including IAM users, groups, roles, and policies. For example, we can use AWS Config to determine the permissions that belonged to a user or group at a specific time. Brilliant post from AWS engineers Chris Grudzinski and Kaustubh Kulkarni, Audit your SAP systems with AWS Config, shows how customers validate that the SAP systems are configured according to best practices, meet the requirements for vendor support, and meet internal audit requirements using AWS Config. AWS Config provides over 160 managed rules, which are rules that have been authored by AWS. We provide a list of the most common rules for SAP workloads to ensure your SAP systems are well architected on AWS below.
- AWS Config Rules allow us to immediate take action after an event has happened, such as isolating resources, enriching the data with additional values or restoring environments to a known-state.
- AWS Trusted Advisor offers a one-view snapshot of our service and helps identify common security misconfigurations, suggestions for improving system performance, and underutilized resources.
And below we have probably most important services for any AWS secure configuration.
- Amazon GuardDuty uses integrated threat intelligence such as lists of known malicious IP addresses, anomaly detection, and machine learning to identify activity associated with threats, such as compromised EC2 instances mining cryptos or an attacker scanning the web servers for known vulnerabilities. It also monitors AWS account access behavior for signs of compromise, such as detecting an atypical instance type deployed by a user from an unusual geo-location, or an attempt to disable CloudTrail logging or to snapshot a database from a suspicious IP address. Escalations of privileges, uses of exposed credentials, or communication with malicious IP addresses are some examples for the detected activities.
- AWS Security Hub provides a single place that aggregates, organizes, and prioritizes our security alerts, or findings, from multiple AWS services and optional third-party products to give you a comprehensive view of security alerts and compliance status.
The combination of GuardDuty and Security Hub provide aggregation, deduplication, and analysis mechanisms for log records coming via other AWS services. GuardDuty ingests, aggregates and analyses information from the VPC DNS service and information.
Security Hub can ingest, aggregate and analyze output from GuardDuty, AWS Config, Amazon Inspector, Amazon Macie, AWS Firewall Manager, among others. Security Hub is often used in combination with world class SIEM solutions as an AWS-side log and alert preprocessor and aggregator.
As SAP experts on AWS, we are committed to helping organisations achieve high levels of security, bringing the benefits of the cloud to those SAP workloads. If you want to know more about innovative and cloud-native solutions in terms of security, you can watch this webinar on demand.
