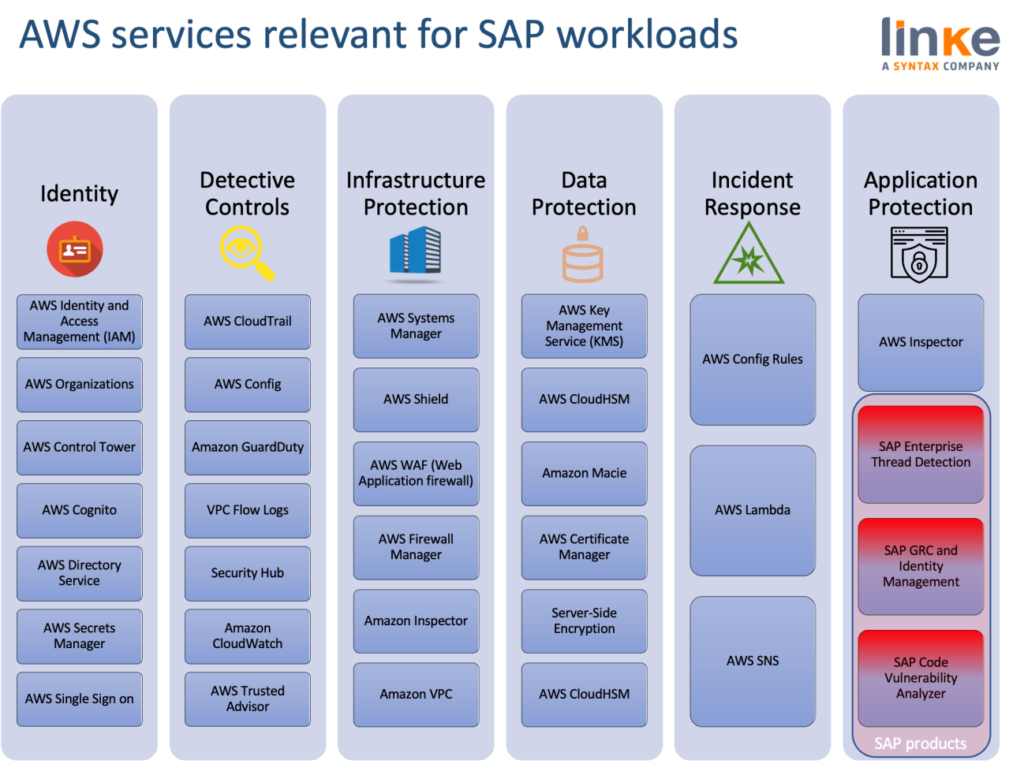
This week our post is dedicated to understanding the most important AWS Services for SAP workloads. This is the third article of the five in the series written by our specialist Mario de Felipe so that companies can address their migrations to the AWS cloud with the necessary security guarantees.
After the two previous blogposts, focused on Identity and Access Management and Detective Controls and Incident Response, it is time to delve into how to safeguard the cloud infrastructure.
AWS breaks Infrastructure Protection down into three broad categories:
- Protecting network and host-level boundaries
- System security configuration and maintenance.
- Enforcing service-level protection.
Protecting Network and Host-Level Boundaries
Protecting Network ensures the first commandment for SAP architectures; Segment SAP workloads with low latency.
Segmenting SAP from other workloads ensures a minimum boundary of trust and inspection. The internal segmentation of application servers, front ends, and databases prevents lateral attacks through impersonation or privilege escalation. Network segmentation is deeply described in these AWS blogs for the VPC setup and configuration of a SAP landscape.
- VPC Subnet Zoning Patterns for SAP on AWS, Part 1: Internal-Only Access
- VPC Subnet Zoning Patterns for SAP on AWS, Part 2: Network Zoning
- VPC Subnet Zoning Patterns for SAP on AWS, Part 3: Internal and External Access
In this series of blog posts, Solution Architects Somckit Khemmanivanh, Harpreet Singh and Derek Ewell introduced Amazon Virtual Private Cloud (Amazon VPC) subnet zoning patterns for SAP applications, demonstrating their use through examples. They describe several architectural design patterns based on access routes, and then follow up with detailed diagrams based on potential customer scenarios, along with configuration details for security groups, route tables, and network access control lists (ACLs).
The extensive AWS documentation helps us understand how to apply the shared responsibility model when using Amazon VPC. The following topics show us how to configure Amazon VPC to meet our security and compliance objectives. We also learn how to use other AWS services that help us to monitor and secure our Amazon VPC resources.
The following recent AWS services will help improving the network setup of our SAP environments:
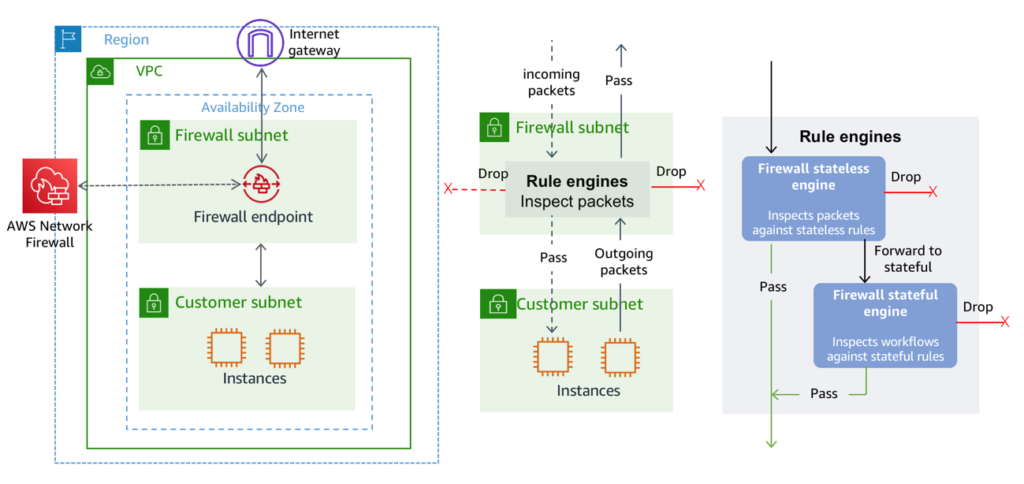
AWS Network Firewall
Brand new, Released Nov 2020, AWS Network Firewall is a stateful, managed, network firewall and intrusion detection and prevention service for our virtual private cloud (VPC).
With Network Firewall, we can filter traffic at the perimeter of our VPC. This includes filtering traffic going to and coming from an internet gateway, NAT gateway, or over VPN or AWS Direct Connect.
Network Firewall is supported by AWS Firewall Manager.
AWS WAF
WAF is a web application firewall that lets us monitor the HTTP and HTTPS requests that are forwarded to an Amazon CloudFront distribution, an Amazon API Gateway REST API, or an Application Load Balancer AWS WAF also lets us control access to our content. Based on conditions that we specify, such as the IP addresses that requests originate from or the values of query strings or different Amazon responds to requests either with the requested content or with an HTTP 403 status code (Forbidden). AWS WAF is a very important service for HTTP SAP services such as Web Dispatcher or SAP Fiori & SAPUI5 components
AWS Shield
We can use AWS WAF web access control lists (web ACLs) to help minimize the effects of a distributed denial of service (DDoS) attack. For additional protection against DDoS attacks, AWS also provides AWS Shield Standard and AWS Shield Advanced. AWS Shield Standard is automatically included at no extra cost beyond what we already pay for AWS WAF and our other AWS services. AWS Shield Advanced provides expanded DDoS attack protection for our Amazon EC2 instances, Elastic Load Balancing load balancers, CloudFront distributions, Route 53 hosted zones, and AWS Global Accelerator accelerators. AWS Shield Advanced incurs additional charges.
AWS Firewall Manager
AWS Firewall Manager simplifies our administration and maintenance tasks across multiple accounts and resources for AWS WAF rules, AWS Shield Advanced protections, and Amazon VPC security groups. The Firewall Manager service automatically applies our rules and other security protections across our accounts and resources, even as we add new accounts and resources.
We can use AWS WAF, AWS Firewall Manager, and AWS Shield together to create a comprehensive security solution for our SAP environment
System Security Configuration and Maintenance
Patching SAP environments, at both the Application, Database and OS level plays a critical role and the most important vulnerabilities have also been discovered and fixed with patches.
AWS Systems Manager
Systems Manager plays a critical role, it allows us to centralize operational data from multiple AWS services and automate tasks across our AWS resources. We can create logical groups of resources such as applications, different layers of an application stack, or production versus development environments. Systems Manager provides a central place to view and manage our AWS resources, so we can have complete visibility and control over our operations.
Amazon Inspector
Amazon Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS. Amazon Inspector automatically assesses applications for vulnerabilities or deviations from best practices. After performing an assessment, Amazon Inspector produces a detailed list of security findings prioritized by level of severity. These findings can be reviewed directly or as part of detailed assessment reports which are available via the Amazon Inspector console or API.
A holistic understanding of SAP resources’ risk posture and compliance levels is critical as SAP is deployed, most important topics where we can use Inspector include locking down OS configuration, administrator with root credentials or HANA services disabling.
AWS Patch Manager
AWS Systems Manager Patch Manager automates the process of patching managed instances with security-related updates. For Linux-based instances, we can also install patches for non-security updates. We can patch fleets of Amazon EC2 instances or our on-premises servers and virtual machines (VMs) by operating system type. This includes supported versions of Windows, Ubuntu Server, Red Hat Enterprise Linux (RHEL), SUSE Linux Enterprise Server (SLES), and Amazon Linux. We can scan instances to see only a report of missing patches, or we can scan and automatically install all missing patches.
SAP Security Updates are periodically released. Customers are recommended to implement patches promptly. However, SAP systems’ uptime requirements create a burden to the SAP basis team to upload, test, and validate every SAP patch. Security-driven networking can help mitigate many risks. Action; get up to date with released SAP security notes frequently, and use above services to automatically patch the SAP systems.
AWS Audit Manager
Introduced just a few months ago, AWS Audit Manager helps us continuously audit our AWS usage to simplify how we manage risk and compliance with regulations and industry standards. AWS Audit Manager automates evidence collection to make it easier to assess whether our policies, procedures, and activities—also known as controls—are operating effectively. When it is time for an audit, AWS Audit Manager helps us manage stakeholder reviews of our controls, which means we can build audit-ready reports like GDPR or GxP with much less manual effort.
AWS Security Hub
Security Hub is designed to give us a comprehensive view of our security posture across our AWS accounts. With Security Hub, we have a single service that aggregates, organizes, and prioritizes our security alerts or findings from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Firewall Manager, AWS System Manager Patch Manager, and AWS IAM Access Analyzer.
AWS Security Hub also integrated with AWS Audit Manager, which helps simplify how we assess risk and monitor our compliance with regulations and industry standards.
Enforcing Service-Level Protection
We can protect AWS service endpoints by defining policies using IAM, described in part 1 of this blog series. IAM can help us define policies for access to services and operations. However, for some services, we can also define fine-grained controls to specific resources within those services. Additionally, some resources have their own resource-level policies.
AWS Key Management Service (KMS)
AWS Key Management Service (KMS) is a managed service that makes it easy for us to create and control the encryption keys used to encrypt our data and uses FIPS 140-2 validated hardware security modules to protect the security of our keys. KMS will be more extensively be explained during the Data Protection series of this blog series.
As SAP experts on AWS, we are committed to helping organisations achieve high levels of security, bringing the benefits of the cloud to those SAP workloads. If you want to know more about innovative and cloud-native solutions in terms of security, you can watch this webinar on demand.
