SECURITY
Azure Sentinel /
Office 365 Defense
Your birds-eye view of cloud security.
Real-time Analysis of Security
Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) platform that uses built-in artificial intelligence (AI) to quickly analyze large volumes of data across an enterprise.
A SIEM provides one central pane of glass for real-time analysis of security alerts generated by applications and network infrastructure. A SIEM reduces the number of people needed to stay on top of security alerts and helps your team focus on security threats that require investigation and remediation. Customized rules can also be implemented to eliminate ‘false positive’ alerts.

Syntax Azure Sentinel Service is Your Birds-Eye View of Cloud Security.
Prevent sophisticated attacks with cloud-native SIEM and security orchestration automated response (SOAR), guided by AI, machine learning (ML), and Syntax’s Security Operations Center (SOC).
With the dramatic rise of cloud adoption, threat hunting must span on-premises and cloud environments. It’s important to collect, detect, investigate, and respond to disparate sources at the massive scale of the cloud in real-time. You can gain peace of mind with the help of cybersecurity tools such as Azure Sentinel that provide intelligent security analytics and threat intelligence. Combine this tool with Syntax’s 24×7 SOC that continuously monitors and responds to security events and you have a big picture view of your cloud security.
What is Azure Sentinel?
Microsoft Azure Sentinel is a scalable, cloud native, SIEM and SOAR solution. Azure Sentinel provides intelligent security analytics and threat intelligence across your enterprise. It provides a single solution for alert detection, threat visibility, proactive hunting, and threat response. Azure Sentinel incorporates proven foundations such as Log Analytics and Logic Apps. Azure Sentinel enriches your investigation and detection with AI and ML. It also provides Microsoft’s threat intelligence stream to help you bring your own threat intelligence to your organization.
Execute Your Cloud Security with Syntax’s SOC
Syntax can help you develop and deploy your cloud security. We combine Syntax’s security strategy with cutting-edge tools such as Azure Sentinel and our 24×7 SOC for monitoring and response. Overcome the growing shortage and high cost of security talent so you can successfully secure your environment and identify and prevent security breaches.
Key Benefits
Azure Sentinel is your expansive view across your enterprise to prevent sophisticated cybersecurity attacks, the rising quantity of security alerts, and long-resolution timeframes.

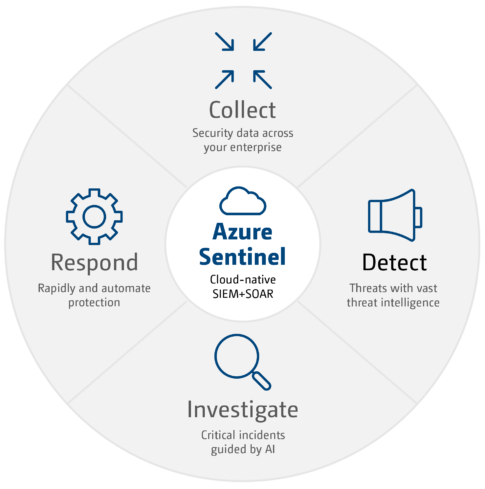
Collect
Gather data at cloud scale across all users, devices, applications, and IT infrastructure located on-premises or in multiple clouds so you can secure it.

Detect
Uncover previously undetected threats. Detect threats with vast threat intelligence. Minimize false positives using Microsoft’s analytics.

Investigate
Guided by AI, find critical incidents. Hunt for suspicious activities at the scale of the cloud.

Respond
Protect your enterprise rapidly and automate common tasks. Respond to incidents quickly with built-in orchestration and automation.
Recognize Value Quickly:
4 Pillars for a Strong Security Posture
Immediately recognize value from the Azure Sentinel solution with Syntax’s experience and proprietary intellectual property (IP). Syntax can rapidly deploy Azure Sentinel, providing you with 24/7 protection and peace of mind. A SIEM project may take a year to get off the ground and it may take your admin weeks or months to set up Azure Sentinel internally. With Syntax, you can be up and running in hours and fully tuned and deployed within a few weeks.

Key Deliverables
- Develop a resource group to separate roles between Syntax and the customer
- Monitor the security alerts; you keep the log data (zero trust model)
- Create an Azure Sentinel-compliant Log Analytics workspace
- Set up, selection, and configuration of Azure Sentinel analytics
- Deploy Azure Sentinel playbooks and workflows
- Automated and integrated incident response program and guided remediation of identified cybersecurity threats
- Implement NIST 800-53 R4 Controls (AU-1 through AU-16) quickly and effectively
