Yesterday, a ransomware codenamed ‘Petya’ began attacking and encrypting data on unpatched Windows computers around the world. Syntax has evaluated this threat and we are pleased to assure everyone that our Private Cloud remains secure, and that none of the clients hosting with us are vulnerable to this threat.
The Petya Ransomware – What You Need to Know
Nonetheless, the Petya ransomware presents a serious threat to the integrity of corporate systems everywhere, and we know that many Oracle Applications users undoubtedly have serious security concerns.
- So Syntax is happy to share our insight and advice with the Oracle ERP end user community.
Petya ransomware threatens servers that have yet not applied the March through May 2017 series of security patches. These include a fix for the ‘MS17-010 Security Update for Microsoft Windows SMB Server’ vulnerability. Different patches will be required based on the operating system version deployed.
And please remember to reboot any newly patched machines.
The Peyta Ransomware Threat – What You Must Do First
Considering the internetworked nature of cloud hosted servers with companies’ local LANs, extranets, 3rd party connections and remote workforces, Syntax strongly recommends:
- Quickly pushing these security patches to your own users and servers.
- Updating all antivirus or endpoint protection modules with the latest signatures.
- If you have internet facing Windows servers or workstations make sure their file sharing ports are not open.
In a worst case scenario, if the Peyta Ransomware threat does strike you these steps will prevent the infection from spreading from one environment to another.
The Peyta Ransomware Threat – Vaccine for Your Computer
There is also a “vaccine” that individual users can implement to protect themselves. Below you can find steps for Windows XP, Windows Vista, Windows 7, and Windows 9 and 10
How to view file name extensions in Windows XP
1. Close all programs so that you are at your desktop.
2. Click on the Start button. This is the small round button ( ![]() ) in the lower left corner of your screen that has a Windows flag on it.
) in the lower left corner of your screen that has a Windows flag on it.
3. When the start menu appears, click on the My Computer menu option.
4. Your My Computer screen should open as shown below.
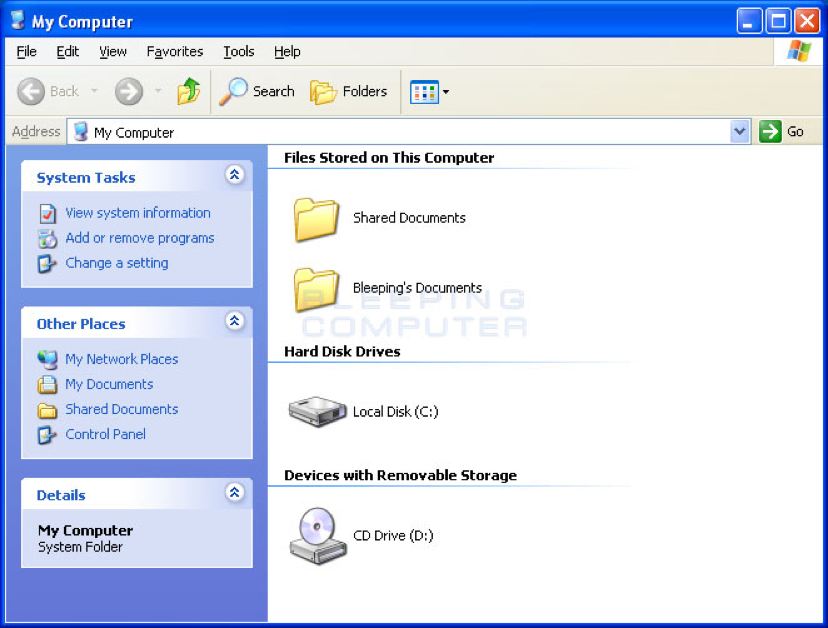
Now click on the Tools menu and select Folder Options….
5. When the Folder Options control panel, please click on the View tab.
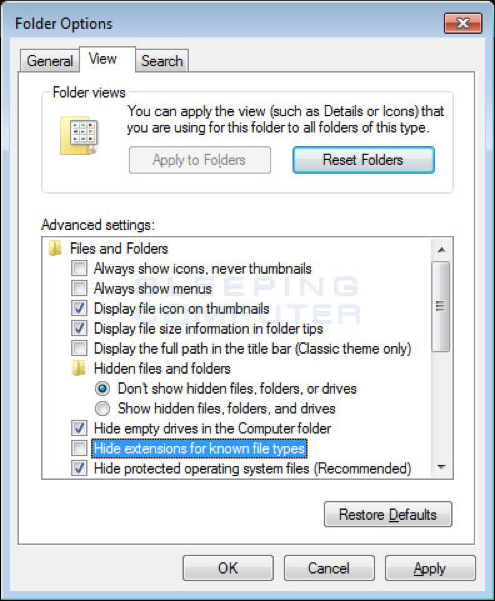
6. You should now see the View tab Folder Options control panel as shown below.
Uncheck the checkbox labeled Hide extensions for known file types.
Once this is done, your Folder Options screen should look similar to the image above.
7. Press the Apply button and then the OK button.
How to view file name extensions in Windows Vista and Windows 7
- Close all programs so that you are at your desktop.
- Click on the Start button. This is the small round button () in the lower left corner of your screen that has a Windows flag on it.
- In the search field type Show hidden as shown in the image below.
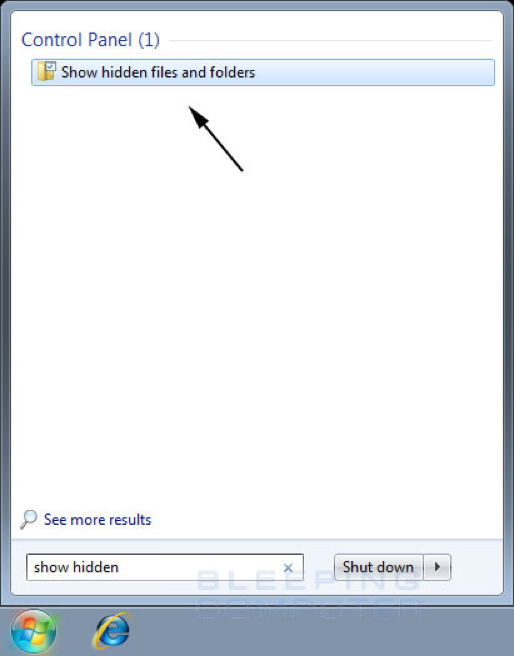
When you see the Show hidden files and folders listing appear, as shown by the black arrow above, click on it to open the Folder Options Control Panel.
4. When the control panel opens, you will see a screen similar to the one below.
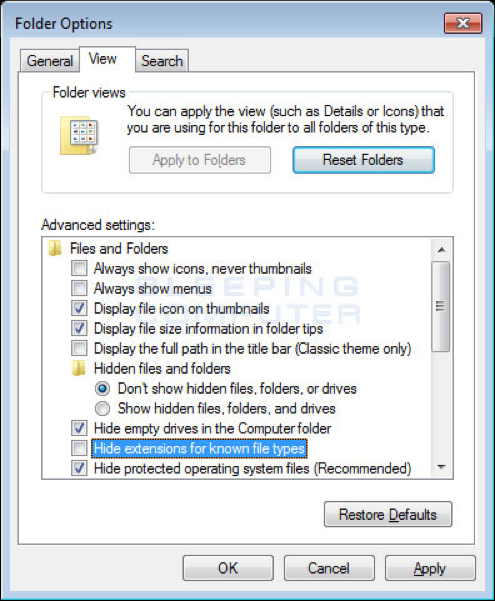
Remove the check mark from the checkbox labeled Hide extensions for known file types. Once this is done, your Folder Options screen should look similar to the image above.
5. Press the Apply button and then the OK button.
You will now be at your desktop and Windows Vista or Windows 7 will be configured to show all hidden files.
How to view file name extensions in Windows 8 and Windows 10
- When in Windows 8 or Windows, open any folder that you wish.
When the folder is opened, please single-click on the View tab. Once you click on this tab, you will be shown a screen similar to the one below.
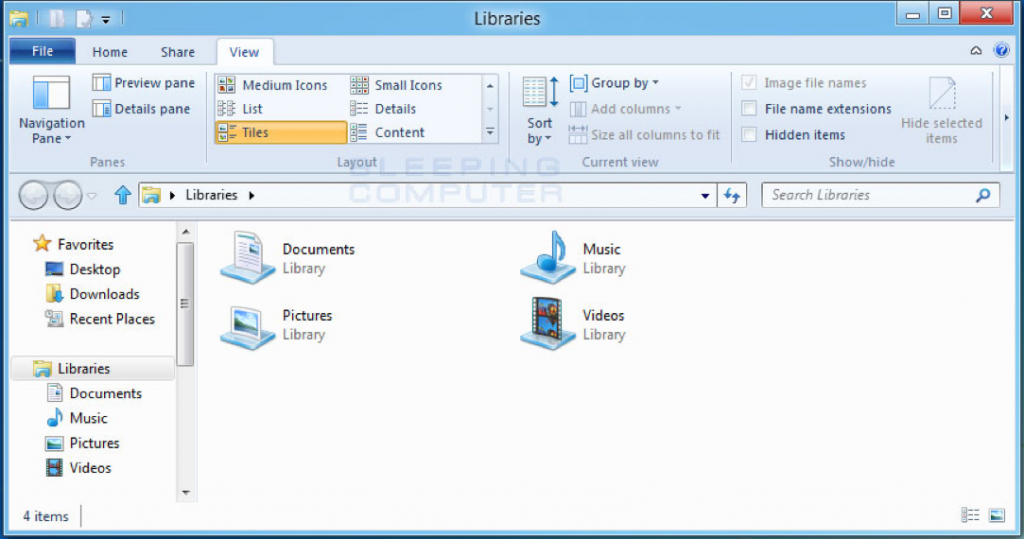
- In this screen, put a check mark in the checkbox labeled File name extensions.
- You can now close Windows Explorer.
You will now be able to see file name extensions in Windows 8.
Once you have enabled the viewing of extensions, which you should always have enabled, open up the C:\Windows folder. Once the folder is open, scroll down till you see the notepad.exe program.
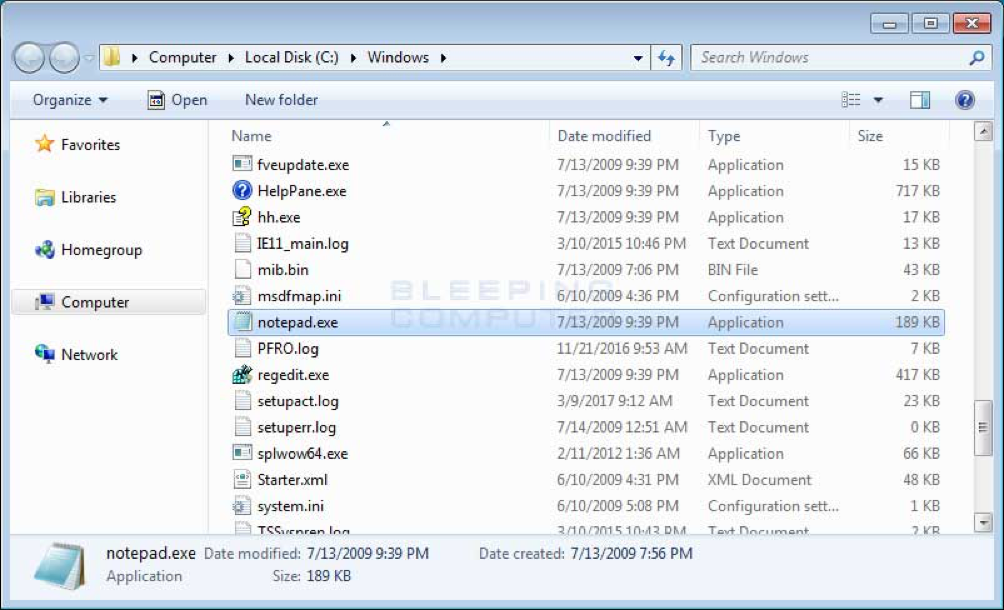
Once you see the notepad.exe program, left-click on it once so it is highlighted. Then press the Ctrl+C to copy and then Ctrl+V to paste it. When you paste it, you will receive a prompt asking you to grant permission to copy the file.
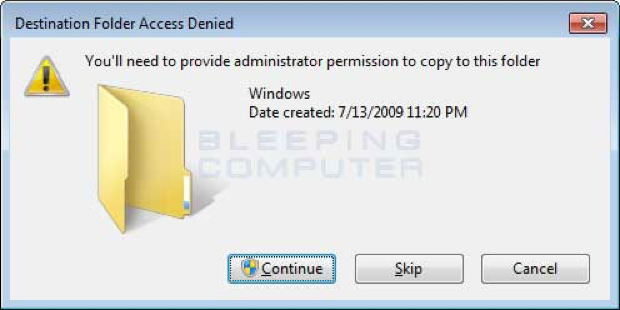
Press the Continue button and the file will be created as notepad – Copy.exe. Left click on this file and press the F2 key on your keyboard and now erase the notepad – Copy.exe file name and type perfc as shown below.
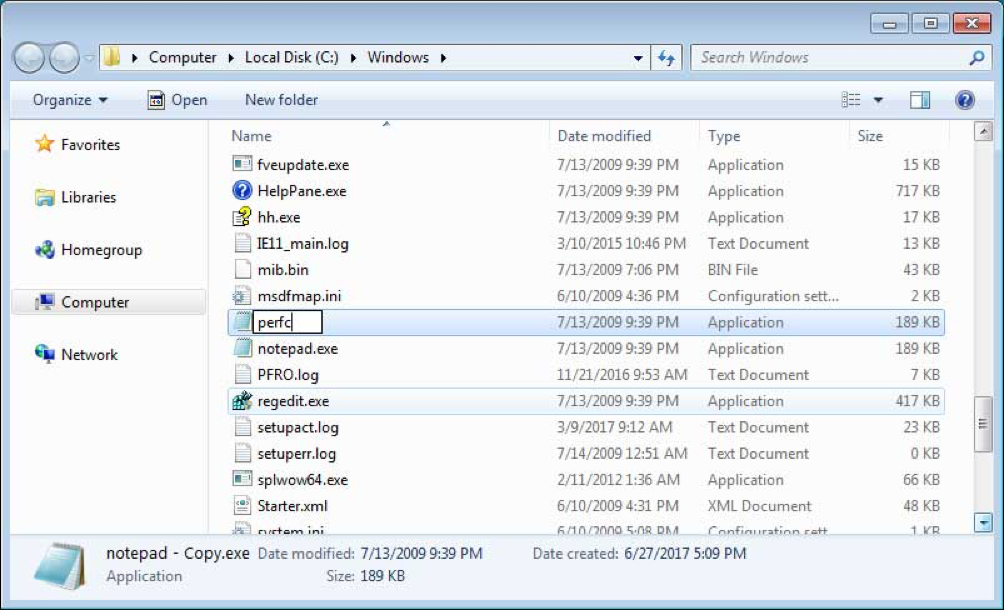
Once the filename has been changed to perfc, press Enter on your keyboard. You will now receive a prompt asking if you are sure you wish to rename it.
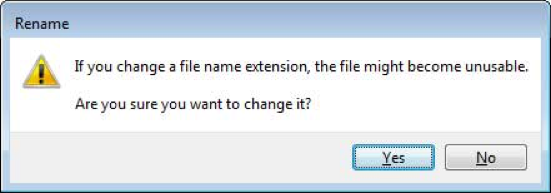
Click on the Yes button. Windows will once again ask for permission to rename a file in that folder. Click on the Continue button.
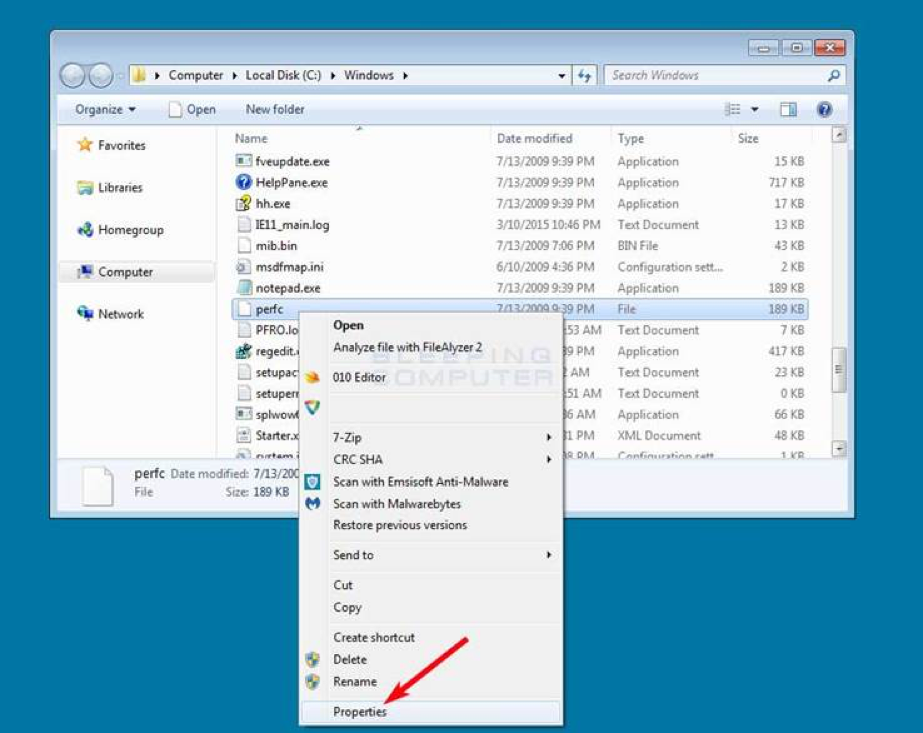
Now that the perfc file has been created, we now need to make it read only. To do that, right-click on the file and select Properties as shown below.
The properties menu for this file will now open. At the bottom will be a checkbox labeled Read-only. Put a checkmark in it as shown in the image below.
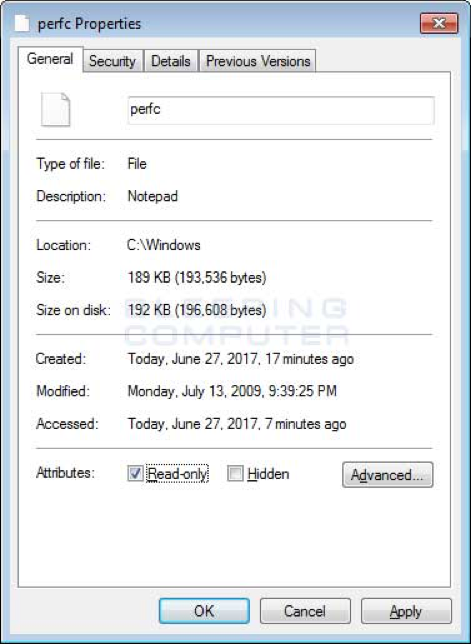
Now click on the Apply button and then the OK button. The properties Window should now close.
For Further Information and Further Action
More information on the patches required, broken down by Windows operating system version can be found here:
https://technet.microsoft.com/library/security/ms17-010#ID0EHB
A special advisory for computers running older WindowsXP and Windows Server2003 to get a one-time patch: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Finally, if you’re an Oracle Applications end user and you want to begin preparing for tomorrow’s enterprise security threat today, we invite you to learn more about Syntax’s Application Managed Services and/or our Private Enterprise Cloud services for JD Edwards and/or Oracle E-Business Suite.
Or if you’re ready to set up a One-on-One with one of our ERP security experts, simply click here to contact us now or simple email us at [email protected].

