In spite of what you might hear, Zero Trust (ZT) isn’t voodoo. It isn’t some black magic secret that nobody can decipher. At its core, Zero Trust Architecture (ZTA) takes a bunch of complex controls and makes them doable. Seamlessly. And your Zero Trust journey starts with your ERP.
Let’s De-Mystify Zero Trust
The National Institute of Standards and Technology (NIST) offers compliance guidelines for Zero Trust under 800-53, 800-171 and 800-207. But perhaps to keep it really simple, we can look at a basic visual to help us understand ZTA.
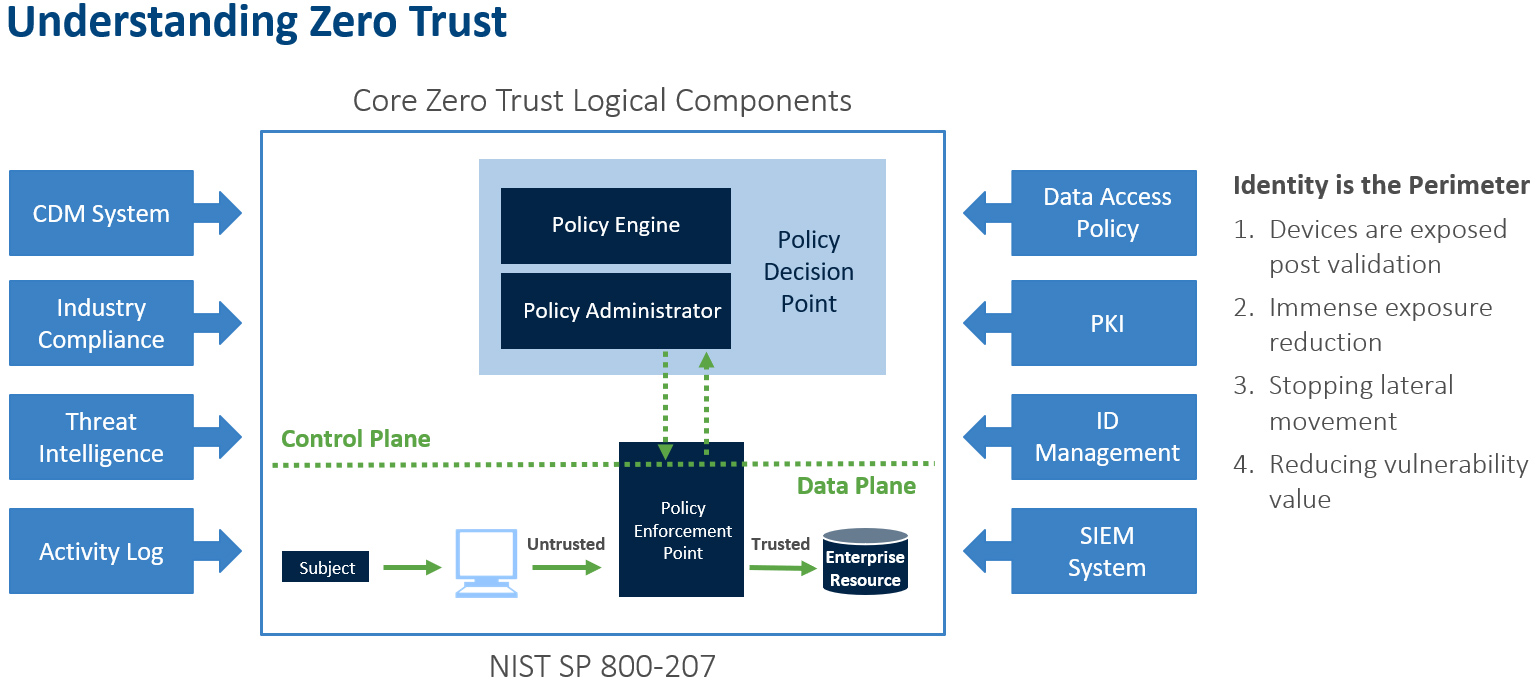
Traditionally, an enterprise’s infrastructure used perimeter-based network security. But that doesn’t work in the face of today’s increasingly complex designs, which might operate several interconnected networks with remote and/or mobile devices and cloud services. By comparison, ZT is not a single architecture but a set of guiding principles for workflow, system design, and operations that can be used to improve the security posture of any classification or sensitivity level.
Transitioning to ZTA is a journey concerning how an organization evaluates risk in its mission, and it cannot simply be accomplished with a wholesale replacement of technology. That said, many organizations already have elements of a ZTA in their enterprise infrastructure. Organizations should seek to incrementally implement zero trust principles, process changes, and technology solutions that protect their data assets and business functions by use case. Most enterprise infrastructures will operate in a hybrid zero trust/perimeter-based mode while continuing to invest in IT modernization initiatives and improve organization business processes.
No Longer Safe
Even if you invested in the best when you first built your network, chances are that your legacy system needs an upgrade in order to maintain security. Zero Trust can reduce your risk by reducing the potential attack surface of your network, based on the identity of those authorized for network access.
Here’s an example:
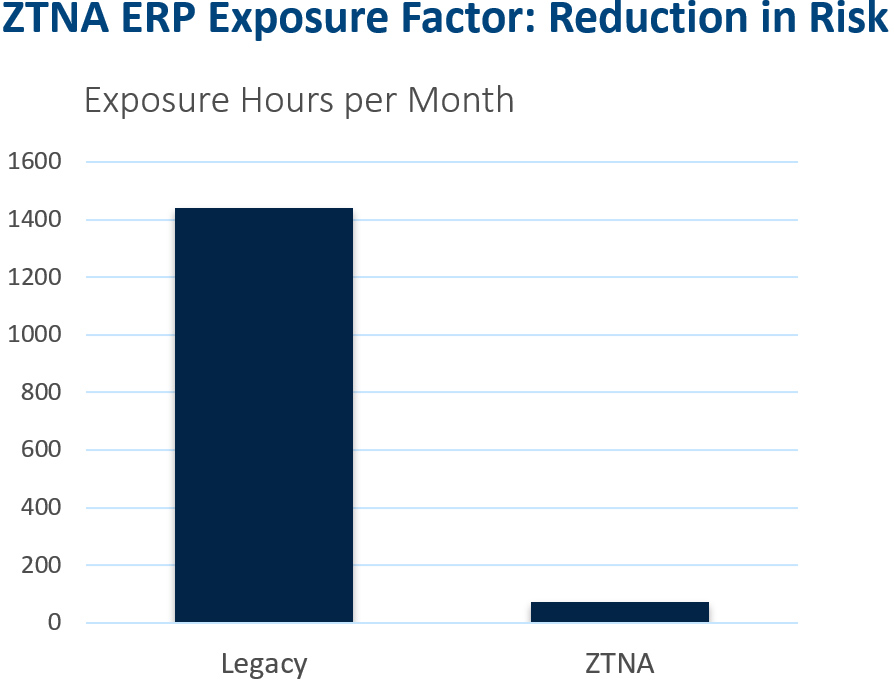
The chart above shows a Legacy/MPLS/VPN for ERP vs ZTNA for ERP. You can see how they compare.
| Legacy/MPLS/VPN for ERP | ZTNA for ERP |
| An ERP system is exposed on VPN/MPLS to 3000 employee and non-employee network assets 24x7x365. | An ERP is exposed to a client system via a single port used and authorized prior to connection. 200 employees have access 5 days a week for 6 hours. |
| At 3% infection rate per month, that’s 90 compromised systems per month at 16 hours per system, or 1440 hours of extreme risk. | At 3% infection rate per month, that’s 6 compromised systems with limited application exposure of 12 hours per system, or 72 hours of moderate risk. |
| There are third-party connectivity points. | There are no third-party connectivity points. |
The Key to Implementing ZT for ERP Is SASE
The road to Zero Trust includes pure ZTA and a hybrid ZTA with an indefinite period when ZTA workflows coexist with non-ZTA workflows in an enterprise (as defined by NIST). The key to this design is the Secure Access Service Edge (SASE).
Coined by Gartner in 2019, SASE, was initially positioned as a pivotal advancement in the digital transformation process: highly customizable network and security services seamlessly stitched into the fabric of a global cloud platform. With a 20% adoption rate expected by 2023, Gartner claimed that the demand for SASE capabilities would “redefine enterprise network and network security architecture and reshape the competitive landscape.”
Since then, the term has spread like wildfire through the IT and enterprise security space. As network security providers and SD-WAN vendors scramble to position themselves as SASE leaders, enterprises are left with a hastily assembled jumble of network and security services that approaches, but often doesn’t fully encompass, a SASE framework.
True SASE adoption requires more than bundling existing single-point solutions — it demands a complete reconsideration of enterprise network infrastructure. Maintaining a rigid on-premise network perimeter is no longer sufficient to protect a distributed, mobile workforce, while juggling multiple security services to protect a hybrid infrastructure can be costly, create headaches for IT teams to deploy and manage, and leave massive security gaps.
SASE addresses these challenges by shifting the network perimeter from centralized data centers to the user. By consolidating networking and network security services and delivering them from a single, cloud-native platform based on Zero Trust principles, SASE eliminates security gaps between services, gives IT teams greater visibility into network activity, and simplifies the cloud migration process.
Zero Trust and SASE: Not Voodoo, Just Greater Security
On-Demand Cybersecurity Executive Forum
Our engaging panel of experts discussed the State of Cybersecurity, Cybersecurity industry trends, why cybercriminal organizations are going straight to your mission-critical ERP systems, which multi-factor authentication is the best, and protecting your “Crown Jewels” while keeping your supply chain safe.
The panel also discussed what criteria companies use in evaluating cybersecurity partners.
About Our Expert
Matthew Rogers
CISO, Syntax
With a demonstrated passion for simplifying complex problems with simple technologies, Rogers has acted as a trusted advisor to CEOs, CIOs and CSOs on cybersecurity during times of crises and prosperity. He has been directly involved with, advised, orchestrated, and or provided boots-on-the-ground strategic response and oversight services for numerous multibillion dollar companies during cyberattacks. He has also designed, implemented, and staffed cybersecurity programs and strategies for the nuclear industry, top-tier HIPAA hosting, and SAP hosting companies. Numerous billion-dollar companies have purchased his consulting services to help them assess and adjust their strategy to help defend against current technical threats such as ransomware. He is also a popular speaker on all cybersecurity topics, including Zero Trust.


