by Matthew Rogers
Global CISO
Syntax
Introduction
With the increasing number of logged threats from cyber-attacks, data breaches, various forms of remote work exposures or bring your own device complexities, it’s important for leaders to implement more secure access control solutions. Many have looked to the Zero Trust architecture, which is one component of how IT security has evolved beyond the once good-enough firewalls of the past.
Let’s start with a definition by the National Institute of Standards and Technology, an authority on this topic, who has published a 59-page document on Zero Trust, NIST.SP.800-207. It serves up Zero Trust as a series of tenets which at its core are the application of both common sense and “defense in depth” strategies.
Defining Zero Trust
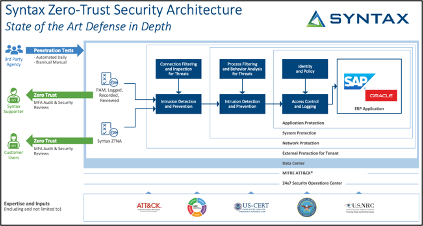
For our purposes here, Zero Trust is a security concept focused on the idea that organizations should not automatically trust anyone or anything inside or outside of their network, whether they are part of the organization or not. This means that organizations should verify the identity of users and devices before granting them access to sensitive information or systems and should continuously monitor and protect their networks to prevent unauthorized access.
An organization can implement a Zero Trust security model by first understanding and documenting its IT landscape, establishing a protection surface, deploying secure access service edge (SASE) solutions, creating an identity-based security policy, and leveraging multi-factor authentication.
For example, identity-based authentication can be used to ensure users are who they say they are and multi-factor authentication can be used to verify they have the necessary privileges to access the system. Companies can also use network segmentation to ensure users can only access the resources they should. Additionally, encryption, monitoring, and other security measures can be used to further secure the network.
Zero Trust and the ERP
ERP systems, such as JD Edwards, are a perfect candidate for the protections of a Zero Trust design. They can be challenging systems to patch with windows for completing that function often having long durations between development, quality assurance, and production environments. ERP systems can never be offline, and they need to be accessible everywhere 24×365. ERP systems function as the figurative brain of the organization and need to be protected.
Cloud-based Syntax Zero Trust Network Access (ZTNA) solutions can be especially beneficial for organizations that have a distributed workforce or that need to access JD Edwards (JDE) from multiple locations. These solutions offer secure access to JDE from any device, anywhere, without the need for VPNs, making it easier for users to access JDE from remote locations. Eliminations of these VPNs offer cost saving opportunities as well as streamlined access management. In summary, using Syntax ZTNA solutions in a cloud environment can provide an additional layer of security for JDE, helping to reduce the risk of unauthorized access or data breaches and ensuring that only trusted users and devices are allowed access.
Syntax Leadership in Zero Trust for JD Edwards
Syntax and JDE means Zero Trust by design. At Syntax we’ve been integrating components of Zero Trust into our solutions for JDE since before Zero Trust became a defined strategy. At Syntax we continuously review the latest security methodologies and concepts against our current designs in concert with a step-by-step assessment for customers as outlined below:
- Needs Assessment:
Start by assessing your security needs and requirements, including the devices and applications that need access to JDE, and the types of data that you need to protect. - Solution Configuration:
Our security experts will configure your ZTNA solution to enforce the policies that you have established for accessing JD Edwards. This typically involves setting up authentication and authorization rules, specifying the devices and applications that are allowed to access JDE, and defining the types of data that can be accessed. - ERP Integration:
Syntax will integrate your ZTNA solution with JDE to ensure that access to the platform is controlled and secure. This typically involves installing client software on the devices that need access to JDE, and configuring the ZTNA solution to work with it - Testing & Validation:
Test your ZTNA solution to ensure that it is working as expected and that access to JDE is secure. This typically involves simulating different access scenarios and verifying that the ZTNA solution is enforcing the access policies that you have established. - Monitoring and Updating:
Syntax will monitor your ZTNA solution to ensure that it is functioning as expected, and update it as needed to stay ahead of emerging security threats.
Explaining the Syntax JDE Zero Trust Baseline
So, what can you expect? Our Syntax framework outlines industry-standard controls across multiple ERPs, leveraging:
- User based multi-factor validation and recorded network access for every session, and every role through Syntax Zero Trust Access
- In-transit inspection and protection of JDE and associated protocols
- Supply chain protection via recorded supporter sessions and enforcement of non-repudiation
- Application based monitoring using Syntax EnterpriseCare© to identify and stop dangerous transactions
- “In-application” monitoring using Syntax FraudID to identify and stop insider-threats
- Data protection in the database using JDE Encrypto to protect from exfiltration
Continuous inspection of all platform code and system code for integrity checking
Syntax & Cloudflare Partner for Zero Trust
Implementing ZTNA for JDE customers dramatically decreases risk by decreasing exposure and increasing visibility of access events. Using ZTNA can decrease reliance on expensive MPLS and VPN connections while increasing responsiveness when powered by world class providers. These benefits have powerful impacts for JDE customers through increasing security, increasing performance, and decreasing costs. Directing system access through ZTNA is a winning strategy for IT leaders in 2023!
Syntax, a multi-cloud multi-ERP leader, has partnered with Cloudflare, which has one of the world’s most powerful networks, to create a Zero Trust ERP specific solution for business. Syntax ZTNA solutions for JDE are available for North American clients.
Click here to speak to a security expert.

